Warning: Locky Ransomware Is Spreading Via Facebook, Linkedin Images; Here Are 2 Ways To Be Protected
Normally, social media portals like Facebook, Linkedin and Twitter are considered safe from the angle of viruses and adware. Users believe and trust these social networks as it is commonly held opinion that content shared on these platforms are rigorously tested and quarantined before making them accessible via their portals and apps.
But Israeli based security consultants have thrashed such pre-conceived notions. As per their latest findings, it was revealed that social media portals like Facebook and Linkedin are being used by hackers to spread a ransomeware named Locky; and thanks to the ignorance of social media users, this is spreading like a wildfire.
Locky Ransomware Spreading Via Facebook, Linkedin
Without revealing the technicalities of the modus-operandi, the researchers at CheckPoint, an Israel based security firm has described how a dangerous ransomeware is spreading via social media networks.
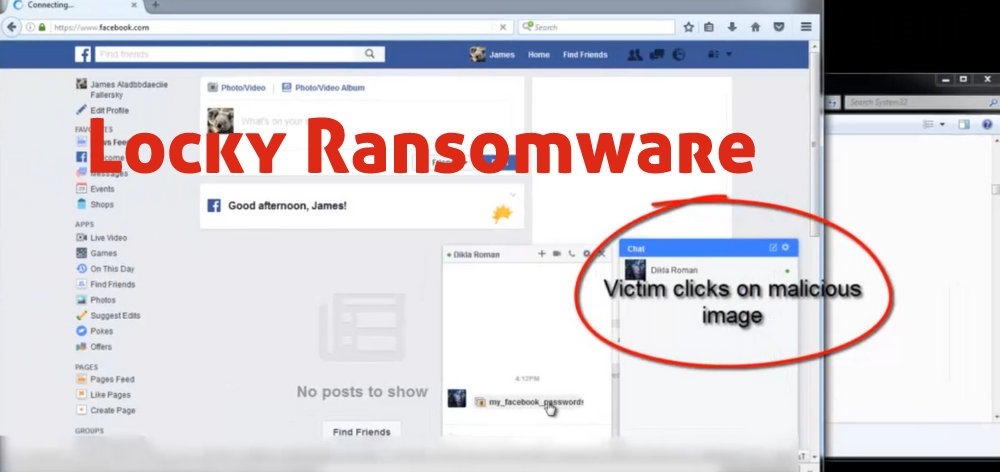
First, the hackers use some hidden techniques to embed a malicious code into any image, which makes it the platform for spreading the virus. Then, that image is uploaded into social media portals like Facebook and Linkedin. Using a security loophole inside social media portals, the malicious code is not detected, and is accessible to the users of that social media.
Using social engineering methods, users are prompted to click on the image, which triggers an automatic download of the same. Now, once the image is downloaded into the internal memory of the user’s computer, the image changes its name, and saves itself.
As soon as the user clicks on the image, the ransomware hijacks every file of the computer, and instructs the user to pay a ransom in order to get back their files. Hijacking is done by encrypting the files and making it inaccessible to the user.
CheckPoint has said that the hackers normally demand a ransom of 0.5 to 1 bitcoin ($220-$450), and unless this is paid, the user is not able to access any file or resource on his own computer.
Locky ransomware emerged early last year as the new form of ransomeware; and its initial spread happened via emails. Hackers attached unpaid MS Word files embedded with Locky ransomware, and named as ‘Unpaid Invoices’. As soon as the user clicks on the invoice, it is auto-downloaded into the users’ computer, and then the ransomware encrypts every file.
The same modus operandi is now used via social media portals.
How To Protect Yourself?
CheckPoint has shared two basic methods, which can prove to be the first line of defense against the ransomware:
a) In case any image gets auto-downloaded into your computer from any social media portal, then don’t click it. First of all, don’t click on any image visible on social media (it can be viewed without clicking on it); and if you have clicked, and it gets downloaded, then don’t click to open it.
b) The downloaded image encrypts itself, and changes the file extension as well. Hence, any dubious image or graphics file in your computer with extension such as SVG, JS, HTA etc can be a potential virus and ransomeware.
Meanwhile, Facebook has denied its involvement in spreading Locky ransomware via its platform. In a statement to Arstechnica, Facebook has blamed some Chrome extensions (or Google indirectly) for the spread of this ransomware.
The statement said, “This analysis is incorrect. There is no connection to Locky or any other ransomware, and this is not appearing on Messenger or Facebook. We investigated these reports and discovered there were several bad Chrome extensions, which we have been blocking for nearly a week. We also reported the bad browser extensions to the appropriate parties.”
Stay vigil and stay alert.
