Malware Becoming A Real Threat For Android Devices In India
With the advent of smartphones, the threats which computers used to face earlier are being passed down to smartphones as well. With the PC market shrinking and the tablets-smartphones growing by leaps and bounds every year, programmers are having a gala time exploiting loopholes. And users are bearing the brunt.
Android had and still has just one issue and that keeps on popping up its head every now and then… Malware. Last month the US Government had said that Android is a malware ‘magnet’, thanks to the OS fragmentation.
The reason was so many devices still run the outdated versions. Of the malicious attacks documented in the study issued by the Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI), 79 percent took place on an Android device. Meanwhile, Apple’s iOS received just 0.7 percent of the recorded malware threats.
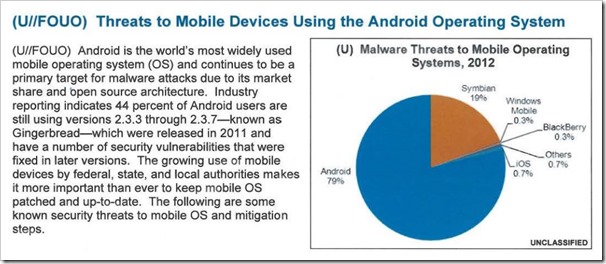
The US report had said that 44 percent of Android users are still using versions 2.3.3 through 2.3.7-known as Gingerbread-which were released in 2011 and have a number of security vulnerabilities that were fixed in later versions.
Now the Computer Emergency Response Team-India (CeRT-In) has said a potentially damaging virus, which steals SMSes and personal details of an Android-enabled gadget-user, has been detected in Indian cyberspace.
The malware is affecting all the versions of Android prior to version 4.2.2 (Jelly Bean). The malicious programme, the advisory said, is so damaging that it could be used for stealing personal information like email addresses, IMEI numbers, SMSes and installed applications. “It could also send SMS or make calls from infected devices without user consent,” the sleuths of the national cyber security centre said.
Modus Operandi
Android Master key vulnerability – The vulnerability involves discrepancies in how Android applications are cryptographically verified & installed, allowing for APK code modification without breaking the cryptographic signature.
All Android applications contain cryptographic signatures, which Android uses to determine if the app is legitimate and to verify that the app hasn’t been tampered with or modified. This vulnerability makes it possible to change an application’s code without affecting the cryptographic signature of the application – essentially allowing a malicious author to trick Android into believing the app is unchanged even if it has been.
The worst part is, the attacker can craft the malicious file for stealing personal information. It could even send SMS or make calls from infected device WITHOUT user consent.
Counter Measures
Check for the permissions required by an application before installing, exercise caution while visiting untrusted sites for clicking links, run a full system scan through a device with a mobile security solution or mobile anti-virus solution or anti-malware software, do not download and install applications from untrusted sources and download applications only from trusted sources, reputed application markets and Google play store.
With Android coming up with newer versions, shouldn’t it join the mobile device manufacturers in providing upgrades to the older handsets – if not all, atleast the major devices using the older versions? Or should the manufacturers be allowed to sell devices with OS which is a sitting duck for hackers, especially when we know it is vulnerable?
