Mobile App Permissions: Biggest Reason For Malware On Android [Study]
Market moves where the customers are. If there are no customers for a product it will get discontinued howsoever good it might be. There are many examples for this including the recent Google Reader.
Unfortunately, along with the market, move the wrong-doers as well. For many years, Microsoft held the baton for the most used OS (Windows) and also the most attacked software. Java is another software widely used and widely abused. Flash has gained such infamy that Apple even banned it completely on its mobile systems. As a software gains prominence, attack on the software increases and its exploitations are more searched for.
Currently the fastest growing OS is Android and hence the most profitable market for crackers or even malware and adware.
According to a McAfee study, in Android, the most crucial way in which Apps exploit are by way of Mobile App permissions.
Most users do not read the app permissions before installing the app. Due to this many apps take more permissions that they actually need and then use these permissions for their advantage.
There are various methods by which an app can misuse its permissions:
Contents
1. SMS Scam:
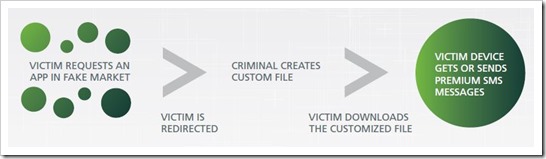
Some apps take permissions to send an SMS from the phone. Now, this permission means that the every time the phone sends an SMS it would be charged on you and you won’t even know this until the bill comes or in case you use a prepaid phone, unless you keep a keen eye on your balance.
In another case, it might be possible that the malware app after installing says that you need to sms on a number to activate the free app. This would again cost you money and many users can get scammed by this.
2. Bogus App Rating:
A malware named FakeRun is tricking users, especially in India, which has the sole purpose of getting its app a 5-star rating. Ratings are very important in the Play Store and if you get a good rating on your app then your other apps also become credible.
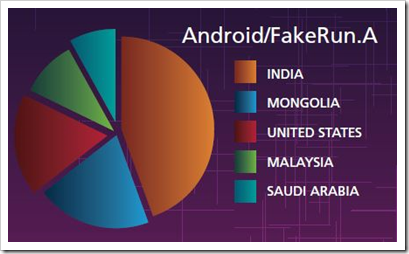
The app asks users to click a button to remove ads and that button gives the app a 5-star rating. After this app gets good ratings the next app by the developer might have an SMS scam malware or even something sinister.
3. Drive-by:
This app installs itself as an update and will start with the phone. This way it won’t have any icon and can’t be shut down or removed easily.
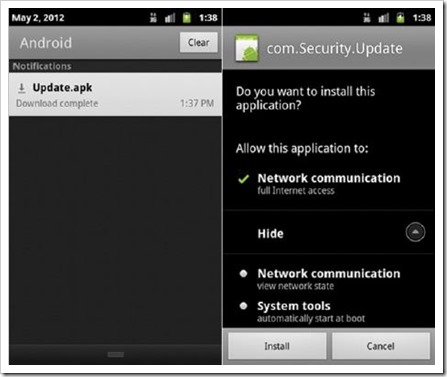
Now, there might be many apps of such kinds that are actually just adware. The developers might sell this data to ad networks and they might use it. But some apps might be even more dangerous and might save information like credit card info etc. These malware apps (because of the permissions) might not even be recognized easily by the user.
This threat is even greater for people whose phones are rooted. Owing to the simple fact, that all of their settings are open to misuse by default, they have to be even more cautious to use their phone.
Apps That Carry Most Malware
McAfee also revealed that games were the most common apps that they found culprit to this followed by Personalization. This sounds perfectly logical as games are the most frequently changed apps on the phone and people are more prone to install a random game than any other kind of app.
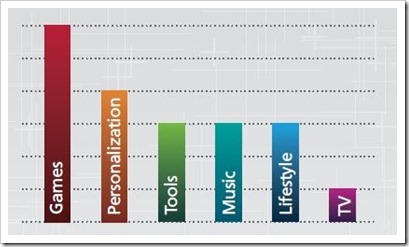
Also, currently Ice Cream Sandwich (4.0) and Jelly Bean (4.1) are most prone to such attacks owing there most prominence.
While Google is taking a lot of steps to remove such nuisances from its store and often removes malware apps, there are still pirated apps and other stores from which a user might install the app and of course, because of the permissions, it is usually after the app has infected some phones that this might come into light.
The bottom line of the research shows that it is up to the users to take care of their phones as was with their laptops and with much more private information saved in the phones, it is even more important that it was for PC. Antivirus are absolutely necessary. And a person should definitely look at the permissions that the app is asking for.
[Source/images: Mcaffee Report]
